Apple Unveils iPhone 16e, The Ultimate Budget Phone with Premium Features promising to Shake...
Tech
If you are Looking for How to Fix “Why is KPLC Paybill Not Working”...
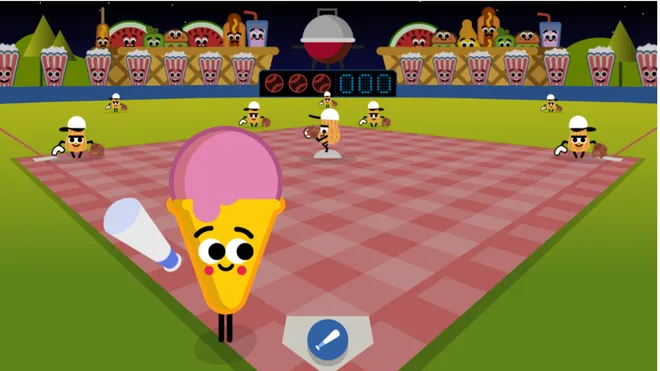
Here’s everything you need to know about Google Doodle Games, A Fun Journey Through...
Here’s everything you need to know about Top AI Innovations to use in Kenya...
Are you Looking for info on KessGame in Kenya? Here’s Everything You Need to...
All about Bitcoin in Kenya Digital Revolution Rush that is Transforming Global Finance and...
If you are Looking for How to Lock Facebook Profile in 2025, you are...
A deep Look at DeepSeek R1 AI that is Revolutionizing AI Innovation and Accessibility...
Samsung Galaxy S25 Ultra: Everything You Need to Know About Samsung’s Next Flagship. As...
Are you looking to Exploring the Buzz Around Trump Coin and Melania Trump Meme...